
Objective
Using a VPN for security and geolocation spoofing.
Background
As part of our post NSA security review, one thing that stood out is the use of our mobile devices in public environments. Anyone can setup a WIFI network and claim it is part of some infrastructure, perhaps even a trusted infrastructure.
Security at WIFI Access Points
A sophisticated criminal can set up the proverbial 'FREE' Internet access point and examine all the inbound/outbound http traffic as well as other non-secure protocols. Personally, I've seen this at conferences. The free fake WIFI access point versus the $35 a day convention WIFI access point. Both the USA and British governments have been accused of setting up both cellular and WIFI mesh networks at high-level conferences/meetings. Then recording everything that is transmitted.
As many mobile apps have a dubious security record for encryption usage and the leakage of data they send to their servers, there is a wealth of information to steal. Lack of HTTPS raises privacy issues just by browsing the Internet. Perhaps you even have an insecure POP or IMAP email connection. This article explains in detail the many insecurities that exist: http://thejh.net/written-stuff/want-to-use-my-wifi
Regardless, government entities are going to record your Internet data at some point. But you can deny the local access point compromise where someone is attempting outright fraud. Even the WIFI access point at a friendly hotel chain might want to collect meta data or perform HTML injection for ads. They are not your friends. Neither is the waiter who double swipes your credit card and is recording all the WIFI traffic in the establishment.
Technology
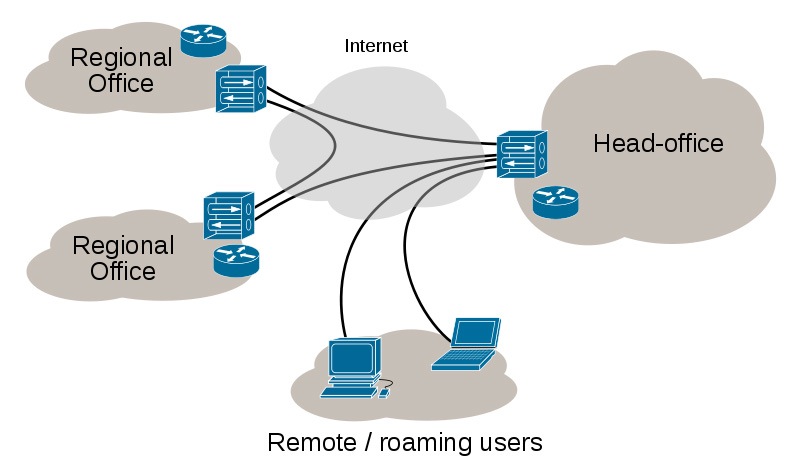
In basic terms, a VPN sets up an encrypted tunnel between you and the VPN endpoint. All the network traffic is routed down that tunnel to the VPN server where it emerges, gets decrypted and is either routed to internal corporate services or to a gateway node then on to the Internet. This serves to deny unencrypted access to the data to nongovernmental actors between the device and the VPN server.
Performance
Any performance problems are distorted by the general timing noise of any public facing provider or across cellular networks. Many professionals now feel this was an excuse to question computationally intensive encryption protocols. Thus pushing vendors or users to cheap protocols which are easily broken, all based on the assumption encryption is slow. Slow in 1993, yes. But not in 2013.
Geolocation
Besides providing encryption between your device and the server, a VPN also offers an anonymous connection to the Internet. The endpoint appears to be a NAT address within the server farm where your VPN gateway is located. Otherwise, a reverse IP Lookup could locate the general location of your mobile device within regional area.
Geographical spoofing via NAT might enable connectivity to resources that attempt to be country location aware. Such as providing access to Pandora Music, a USA only offering. This of course can be defeated if the service demands mobile device GPS location data as part of their service agreement.
VPNs do not offer true anonymous access because a financial paper trail still exists. Any legit players in this area have backed away from claiming your access is anonymous to government authorities. If you think a VPN can truly hide your internet usage, think again.
Your geolocation aware service provider may block the hosting server farm in this game of hide and seek. Athough a commercial VPN service offering is identifiable to the service, blocking all of Amazon is usually infeasible. With a Amazon Elastic Compute Cloud (EC2) box, a VPN server costs about $5 a month (paid at the yearly rate) and gives you total control over the offering, as well as the headaches of server management.

Details
A VPN can be implemented via three different internet protocols which are used to create the tunnel, manage, and support the type of encryption and checksums used. To make the USA government happy, most offerings settle on the weakest security setup which is based on the Windows XP hosted protocol called PPTP. Do not use this. The security is broken.
The other two protocols in use are L2TP and IPSec, but telcos generally block the L2TP+SSL protocol. That leaves IPSec which provides strong encryption and is usually implemented by a Cisco network appliance run by a corporation server farm. Therefore, IPSec is unblocked by telcos because corporations run VPNs over mobile networks and wisely don't consider PPTP. This leaves the telco no choice but to unblock or charge you an extra fee for the service. Note: to use a VPN you might have to become a business customer instead of a regular user. Telco to telco policy is different. As an example, on USA ATT customer cellular L2TP is blocked; but IPSec is not.
A WIFI access point might potentially block VPN traffic. They are not your friends if they do that. In a commercial setting, such as a hotel, there might be a VPN aware offering, usually at additional cost for the business users. Other situations, like schools, may block VPN to prevent anonymous Internet usage, as they enforce a restricted Internet access environment using a whitelist of acceptable domains. Unfortunately there is no workaround for that situation.
Assuming IPSec works, the other consideration is the encryption and hash protocols to use. But beware… to pacify the USA government, the weakest or the broken choices are the default settings out of the box. If you are not buying a Cisco box, a software solution is necessary. There are free and paid choices, so pick the free open source solution.
Configuration requires extensive backgrounds in network setup and server management If you are not familiar with “config” and “make” you will need to have an expert set this up. On a consulting basis, I can assist in setting up a solution assuming you have a Amazon AWS account. Email me here.
Our choice is to use the Switzerland based open source project called Strongswan. http://strongswan.org

Strongswan Install
Configure a Amazon EC2 Micro Instance. In this example, I used an Amazon Ubuntu 12.04 server setup.
Pull the latest stable Strongswan version from the vendor as it is needed for iOS 7.
Wget http://download.strongswan.org/strongswan-5.1.0.tar.bz2 ensure you pick latest.
To compile, you will need the OpenSLL development environment.
aptitude install openSSL
aptitude install libssl-dev
Configure Strongswan
./configure --prefix=/usr --sysconfdir=/etc --disable-gmp --enable-eap-gtc --enable-openssl
make
make install
It is possible some subcomponent are missing and require more install commands.
Configuration Certificates for the Server and the Client
Assuming you want a self signed certificate then follow the instructions at:
http://wiki.strongswan.org/projects/strongswan/wiki/IOS_(Apple)/9
The resulting certificates are used on the device, and on the server.
/etc/ipsec.conf
Config setup:
conn ios
keyexchange=ike
authby=xauthrsasig
xauth=server
left=%defaultroute
leftsubnet=0.0.0.0/0
leftfirewall=yes
leftcert=serverCert.pem
right=%any
rightsubnet=10.0.0.0/24
rightsourceip=10.0.0.0/24
rightcert=clientCert.pem
auto=add
esp=aes256-sha1!
ike=aes256-sha1-modp1536!
#include /var/lib/strongswan/ipsec.conf.inc
Indicate the order of strong encryption choices to negotiate for ESP and for IKE (initial key exchange). Otherwise a less secure default choice is made.
The ESP & IKE chosen are AES 256 bits, SHA1 for the hash and 1536 bits for DFH key exchange. These are the maximum supported encryption and hash protocols for iOS devices.
The leftcert and rightcert define the certificates to use, either self signed or from a certificate authority.
/etc/ipsec.secrets contents
: RSA serverKey.pem
USERID : XAUTH “PASSWORD”
Provide one entry for each device user. Do not share a sole user ID and mobile configuration file between multiple devices because a duplicate login will terminate any stale or other active connections using those login credentials.
/etc/strongswan.conf - strongSwan configuration file
Set both charon and pluto dns1 and dns2 to Google's DNS servers 8.8.8.8 and 8.8.4.4
Network Ports
To support just IPSec you need to open port UDP 500
iOS Device Provisioning File(s)
Use Apple’s iPhone configuration utility to specify the details of the VPN and to include the server’s public certificate. Then extrude the provisioning file as XML. As the IOS 6 configuration tool lacks some IOS 7 features, add the additional XML below to enable on-demand VPN by interface type
<key>OnDemandEnabled</key>
<integer>1</integer>
<!-- on demand rules -->
<key>OnDemandRules</key>
<array>
<dict>
<key>Action</key>
<string>Connect</string>
<key>InterfaceTypeMatch</key>
<string>WiFi</string>
</dict>
<dict>
<key>Action</key>
<string>Connect</string>
<key>InterfaceTypeMatch</key>
<string>Cellular</string>
</dict>
</array>
<!-- on demand rules -->
Certificates
In order to trust the secure connection, the self-signed server public certificate must be on the device as a separate provisioning file. Otherwise, if the SSL server was purchased from an ICANN certificate authority, the certificate is fetched from the server and the chain of signing authority validates the certificate trust.
Sorry, no implementation thoughts for Android. Search the Internet for IPSec setup directions.
Activating the VPN
A number of solutions exist with iOS 7:
(A) Manual on/off. This is not recommended.
(B) VPN activation can be based on DNS name lookup failure, host lookup failure or URL fetch failure.
The VPN is not activated until an attempt is made to access a service hidden within the VPN service by the wildcard name, DNS server lookup or URL fetch. If the request fails, the VPN is automatically started and the request is made again. As an example, connect to musicmusicmusic.com. First check to see if connection to https://www.ourserver.com/nonexistent_url works. if it does not, activate the VPN and try the connection to musicmusicmusic.com.
<key>OnDemandEnabled</key>
<integer>1</integer>
<!-- on demand rules -->
<key>OnDemandRules</key>
<array>
<dict>
<key>Action</key>
<string>EvaluateConnection</string>
<key>ActionParameters</key>
<array>
<dict>
<key>Domains</key>
<array>
<string>musicmusicmusic.com</string>
</array>
<key>RequiredURLStringProbe</key>
<string>https://www.outserver.com/nonexistent_url</string>
<key>DomainAction</key>
<string>ConnectIfNeeded</string>
</dict>
</array>
</dict>
</array>
<!-- on demand rules -->
This is overly complex and I would not recommend using this solution.
(C) VPN startup on network interface activation, a new IOS 7 feature. This solution is the best choice and applies to WIFI and cellular, although Bluetooth and tethered connections by the device also exist.
Sadly, a bug or feature exists in IOS (A single interface aware VPN which is set to Connect by Demand) means the VPN will auto start even if the master VPN switch is set to OFF. To disable the VPN start the iOS Settings.app, choose the VPN setup, turn “Connect on Demand" OFF for the network choice, then turn the master VPN switch OFF. But a more simple option is to create a fake VPN setup, choose it and switch the master VPN switch off
Security issues
The user ID and passwords are exposed both in server file and in the provisioning file. Don't use anything related to real user IDs and passwords. The user ID and password can be blank on the device and then entered as needed. However, in an intermittent cellular connectivity situation, the prompts on each cellular hiccup reconnect are disruptive.
Even if there is a valid user id and password, the self signed certificate situation still requires the self signed public certificate on the device.
Diagnostics
On the server, issue the following command to identify active connections:
ipsec statusall
Status of IKE charon daemon (strongSwan 5.1.0, Linux 3.2.0-56-virtual, i686):
uptime: 50 minutes, since Nov 16 21:25:52 2013
malloc: sbrk 294912, mmap 0, used 144200, free 150712
worker threads: 11 of 16 idle, 5/0/0/0 working, job queue: 0/0/0/0, scheduled: 8
loaded plugins: charon aes des rc2 sha1 sha2 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey pem openssl fips-prf xcbc cmac hmac attr kernel-netlink resolve socket-default stroke updown eap-gtc xauth-generic
Virtual IP pools (size/online/offline):
10.0.0.0/24: 254/1/0
Listening IP addresses:
10.244.9.###
Connections:
ios: %any...%any IKEv1/2
ios: local: [C=CA, O=mycompany, CN=vpn.mycompany.net] uses public key authentication
ios: cert: "C=CA, O=mycompany, CN=vpn.mycompany.net"
ios: remote: [C=CA, O=mycompany, CN=client] uses public key authentication
ios: cert: "C=CA, O=mycompany, CN=client"
ios: remote: uses XAuth authentication: any
ios: child: 0.0.0.0/0 === 10.0.0.0/24 TUNNEL
Security Associations (1 up, 0 connecting):
ios[4]: ESTABLISHED 14 seconds ago, 10.244.9.###[C=CA, O=mycompany, CN=vpn.mycompany.net]...66.65.73.##[C=CA, O=mycompany, CN=client]
ios[4]: Remote XAuth identity: USERID
ios[4]: IKEv1 SPIs: d0ac799abf12aa8b_i 7f5fbf241dfc9f88_r*, public key reauthentication in 2 hours
ios[4]: IKE proposal: AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536
ios{2}: INSTALLED, TUNNEL, ESP in UDP SPIs: cdbe8b26_i 0b5504b5_o
ios{2}: AES_CBC_256/HMAC_SHA1_96, 34774 bytes_i (295 pkts, 7s ago), 82654 bytes_o (267 pkts, 7s ago), rekeying in 42 minutes
ios{2}: 0.0.0.0/0 === 10.0.0.1/32
Finally, consider using the VPN server machine for other purposes like a NGINX static web server.

I Can Help
Again, contact me at johnmci@smalltalkconsulting.com. I will be happy to provide consulting to setup up your VPN.